CS 3IS3 Assignment #3
CS 3IS3
Assignment #3. Due Wednesday April 14, details 2021, 23:59 via Avenue. Do not hesitate to discuss with TA or instructor all the problems as soon as you discover them.
The deadline for this assignment CAN NOT be postponed!!
This assignment consists of many questions but most of them are rather easy.
Instructions: For Each Assignment, students must submit their solution to Avenue > Assessments > Quizzes > Assignment #
For each question, students will have a rich format text box for each question in the avenue which also allows them to copy and paste their solutions directly from Microsoft word in to the text box or attach an image file or pdf file or other required files to that text box. Please first finish the assignment on your local computer and at the end, copy and paste their solution to each avenue textbox or attach your solution as a PDF file for each question separately. The suggested format for the attached image files is .jpg or .png format. Make sure to save you work for each question in avenue by clicking on the outside of the textbox box in avenue, will allow avenue you save your response. If a student need to scan a hand written note and insert it into the textbox is encouraged to use a smartphone app called CamScanner).
PLEASE DO NOT USE THE SUBMIT button every time to SAVE your work. Only use the submit button for your final submission.
Student can easily create a snap shot of their hand written solutions or diagrams by using windows snipping tool (Grab for Mac) with these tools students can save the image as .png file and then attach it to each textbox at the end after they finalized their solution.
Students, who do not have Microsoft Word on their computer, are suggested to use google document editor (Google Docs).
There will be a mark deduction for not following the submission instruction.
Students must submit their assignments to Avenue. Any problem with Avenue, please discuss with Mahdee Jodayree <[email protected]>, a TA for this course.
For the questions involving programming you should provide a Java program together with the corresponding instructions on how to compile it and run some test cases; good programming style will also be marked.
Furthermore, for each one of the questions involving Java, you must also submit an explanation in what way your Java program implements your model.
Total number of points: 186
1.[8] In addition to stack-based buffer overflow attacks (i.e., smashing the stack), integer overflows can also be exploited. Consider the following C code, which illustrates an integer overflow
a.[6] What is the potential problem with this code?
Hint: The last argument to the function memcpy is interpreted as an unsigned integer.
b.[2] Explain how an integer overflow might be exploited by Trudy.
2.[10] Consider the following protocol for adding money to a debit card.
(i) User inserts debit card into debit card machine.
(ii) Debit card machine determines current value of card (in dollars), which is stored in variable x.
(iii) User inserts dollars into debit card machine and the value of the inserted dollars is stored in variable y.
(iv) User presses enter button on debit card machine.
(v) Debit card machine writes value of x + y dollars to debit card and ejects card.
Recall the discussion of race conditions in the text. This particular protocol has a race condition.
a.[2] What is the race condition in this protocol?
b.[6] Describe a possible attack that exploits the race condition.
c.[2] How could you change the protocol to eliminate the race condition or at least make it more difficult to exploit?
3.[8] Suppose that you are asked to design a metamorphic generator. Any assembly language program can be given as input to your generator, and the output must be a metamorphic version of the input program. That is, your generator must produce a morphed version of the input program and this morphed code must be functionally equivalent to the input program. Furthermore, each time your generator is applied to the same input program, it must, with high probability, produce a distinct metamorphic copy. Finally, the more variation in the metamorphic copies, the better. Outline a plausible design for such a metamorphic generator.
4.[8] Suppose that you are asked to design a metamorphic worm, where each time the worm propagates, it must first produce a morphed version of itself. Furthermore, all morphed versions must, with high probability, be distinct, and the more variation within the metamorphic copies, the better. Outline a plausible design for such a metamorphic worm.
5.[6] Consider the code on page 28 of LN 16 or in Table 11.5 of the textbook, which is susceptible to a linearization attack. Suppose that we modify the program as follows:
Note that we never break out of the for loop early, yet we can still determine whether the correct serial number was entered. Explain why this modified version of the program is still susceptible to a linearization attack.4
6.[9] Suppose that a bank does 1000 currency exchange transactions per day.
a.[3] Describe a salami attack on such transactions.
b.[3] How much money would Trudy expect to make using this salami attack in a day? In a week? In a year?
c.[3] How might Trudy get caught?
7.[8] The goal of this problem is to show that you can convert any conditional into an opaque predicate.
a.[3] Given the conditional
if (a < b)
// do something
else
// do something else
slightly modify the if statement so that the do something branch always executes.
b.[2] Explain why your solution to part a will work in general.
c.[3] How stealthy is your approach, that is, how difficult would it be for an attacker to (automatically) detect your opaque predicates? Could you make your approach stealthier?
8.[7] Once a user authenticates, it is sometimes desirable to have the program keep this authentication information available, so that we do not need to bother the user to authenticate repeatedly. This could also be viewed as a form of single sign-on
a.[4] Devise a method for a program to cache authentication information, where the information is stored in a different form each time it's cached.
b.[3] Is there any security advantage to your approach in part a, as compared to simply storing the information the same each time?
9.[7] Once a user authenticates, it is sometimes desirable to have the program keep this authentication information available, so that we do not need to bother the user to authenticate repeatedly (this could be viewed as a form of single sign-on)
a.[4] Devise a method for a program to cache authentication information where the information is stored in a different form each time it's cached.
b.[3] Is there any security advantage to your approach in part a, as compared to simply storing the information the same each time?
10.[10]Suppose that a large and complex piece of software has 10,000 bugs, each with an MTBF of 1,000,000 hours. Then you expect to find a particular bug after 1,000,000 hours of testing, and - since there are 10,000 bugs - you expect to find one bug for every 100 hours of testing. Suppose the good guys do 200,000 hours of testing while the bad "guy," Trudy, does 400 hours of testing.
a.[2] How many bugs should Trudy find? How many bugs should the good guys find?
b.[8] What is the probability that Trudy finds at least one bug that the good guys did not?
11.[12]This problem compares closed systems and open systems.
a.[3] Define "open system" and give an example of an open system.
b.[3] Define "closed system" and give an example of a closed system.
c.[3] What are the advantages of open systems, as compared to closed systems?
d.[3] What are the advantages of closed systems, as compared to open systems?
12.[8] Suppose that there are 100 security flaws in a particular software project and we can list these flaws in such a way that security flaw i requires i hours of testing to find. That is, it takes one hour to find flaw number one, two more hours to find flaw number two, three more hours to find flaw number three, and so on. What is the MTBF for this system?6
13.[6] This problem deals with mandatory access control (MAC) and discretionary access control (DAC).
a.[2] Define the terms mandatory access control and discretionary access control.
b.[2] What are the significant differences between MAC and DAC?
c.[2] Give two specific examples where mandatory access control is used and give two examples where discretionary access control is used.
14.[6] In the class we discussed segmentation and paging.
a.[2] What are the significant differences between segmentation and paging?
b.[2] Give one significant security advantage of segmentation over paging.
c.[2] What is the primary advantage of paging over segmentation?
15.[8] In the class we briefly compared blacklisting and whitelisting.
a.[2] What is blacklisting?
b.[2] What is whitelisting?
c.[2] As a general security principle, which is preferable, whitelisting or blacklisting? Why?
d.[2] Which is likely to be more convenient for users, blacklisting or whitelisting? Why?
16.[4] It is sometimes argued that digital rights management (DRM) is, in some sense, the modern incarnation of multilevel security (MLS).
a.[2] List some significant similarities between DRM and MLS.
b.[2] List some significant differences between DRM and MLS.
THE LAST 6 QUESTIONS DEAL WITH ‘ADVANCED CRYPTOANALYSIS’ (LN 22-23, Chapter 6 of the textbook). For some questions writing and then using some programs (in Java, C, C++, etc.) could be helpful.
17.[12]Find a 16-bit key that encrypts
plaintext = 0x1223 = 0001001000100011
to
ciphertext = 0x5B0C = 0101101100001100
using the cipher TDES.
Hint. Write a program (in Java, C, C++, etc.) which can do an exhaustive key search.
18.[12]Construct a difference table analogous to that on page 13 of LN 22 and in Table 6.6 in the textbook and for S-box 1 of DES. The DES S-box 1 appears on page 17 of LN2 and in Table 3.3 of Chapter 3.
What is the most biased difference and what is the bias?
19.[12]Construct a linear approximation table analogous to that on page 16 of LN27 and in Table 6.7 for the left S-box of TDES. Verify the results of equations y1 = x2 and y2 = x3 (page 36 of LN22 and the equation (6.29) in the textbook). What is the next best linear approximation and how well does it approximate?
20.[8] Recall the linear cryptanalysis of TDES discussed in LN22 and in Section 6.4.6. of the textbook. Assume that equation k0 ⊕ k1 = c1 ⊕ p10 (page 38 of LN22 and (6.33) in the textbook holds with probability (3/4)3 ≈ 0.42. Also assume that the key satisfies k0 ⊕ k1 = 0. Then if we conduct the attack using 100 known plaintexts, what are the expected counts for c1 ⊕ p10 = 0 and c1 ⊕ p10 = 1 ? Compare your answer with the empirical results presented in the text. Why do you think the theoretical and empirical results differ?8
21.[7] Consider the "simple" timing attack on RSA discussed in Section 6.6.1 of the textbook and LN23.
a.[4] Extend the timing attack to recover the bit d2. That is, assuming that bit d1 has been recovered, what conditions must Y and Z satisfy so that the attack presented in the text can be used to determine d2?
b.[3] In practice, we need to recover about half of the private key bits. Why is this attack not a practical means for recovering such a large number of private key bits?
22.[10]This question requires additional reading. Read the Chapter 6.6.2 about Kocher's Timing Attack.
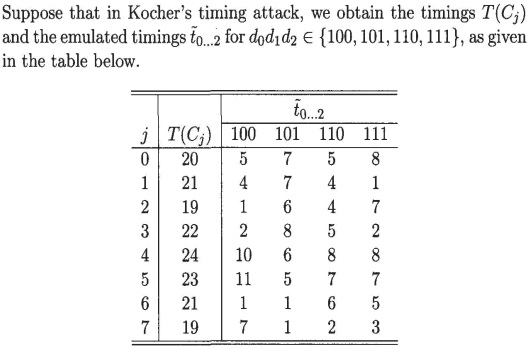
a.[5] What is the most likely value of d0d1d2 and why?
b.[5] Why does this attack not succeed if CRT or Montgomery multiplication is used?
2021-03-25

