Assignment 6: Simple Layer 2 Firewall
Hello, dear friend, you can consult us at any time if you have any questions, add WeChat: daixieit
Assignment 6: Simple Layer 2 Firewall
For this assignment you will use Mininet and the POX SDN controller to implement a simple layer 2 (the link layer) firewall application that blocks traffic from (source, destination) pairs of MAC addresses in a policy file.
A firewall is a “ middlebox” that monitors network traffic and decides whether to allow or block specific traffic based on a defined set of security rules (the firewall “ policy”). Most production-level firewalls make allow/block decisions by looking at information from several layers of the protocol stack (e.g. transport and application layers), and also maintain state information about packet flows to use in the decision making process.
Your firewall will be a simple link layer firewall that sends flow rules to a switch which will examine one packet at a time. This type of firewall is usually referred to as a “ packet filter” .
Here is the network architecture you will use:
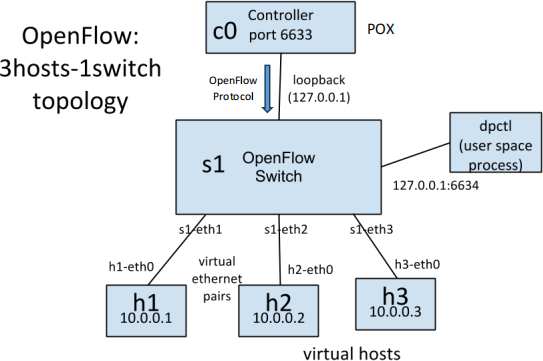
POX is an SDN controller that works with OpenFlow switches, such as Open vSwitch, used by Mininet POX is written in Python and is easy to extend by adding your own code.
You can set up the Mininet environment above (except for the controller) with this command:
$ sudo -E mn --topo single,3 --mac --switch ovsk --controller remote
The --controller remote switch tells Mininet not to use the built-in controller, instead we will use POX as our (remote) controller. This means that POX is ‘c0’ in the diagram above. The --mac switch tells Mininet to use simple MAC addresses, e.g. 00:00:00:00:00:01, 00:00:00:00:00:02, and so on.
POX
Documentation for POX is available here:https://openflow.stanford.edu/display/ONL/POX+Wiki
If you are using the pre-built Mininet VM, POX is already installed in /home/mininet/pox.
We can run POX as follows:
$ cd ~/pox
$ sudo -E python3 pox.py forwarding.l2_learning
The POX controller will listen on TCP port 6633. Mininet’s switch will automatically try to connect to it (since we specified --controller remote). Note that POX uses a peculiar syntax for identifying and loading modules. Specifying forwarding.l2_learning tells POX to look in pox/pox/forwarding for a module called l2_learning.py and loads it. The l2_learning module implements a simple layer 2 learning switch. We will add a module called comp4911.l2fw in pox/pox/comp4911/l2fw.py to implement a simple layer 2 firewall.
dpctl
The dpctl command is a utility that we can run form the mininet> prompt to communicate with the switch (‘s1’). We will use it to dump the switch flow table.
The flow table is what the switch uses to decide what to do with packets it receives. For our purposes, the flow table can be thought of as a forwarding table.
Let’s send a ping from h1 to h2, and use ‘dpctl dump-flows’ to look at the flow table:
mininet> h1 ping -c 1 h2
PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data.
64 bytes from 10.0.0.2: icmp_req=1 ttl=64 time=65.5 ms
--- 10.0.0.2 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 65.588/65.588/65.588/0.000 ms
mininet> dpctl dump-flows
*** s1 ---------------------------------------------------------------
cookie=0x0, duration=2.286s, table=0, n_packets=1, n_bytes=98,
idle_timeout=10, hard_timeout=30, priority=65535,icmp,in port="s1-
eth1",vlan_tci=0x0000,dl_src=00:00:00:00:00:01,dl_dst=00:00:00:00:00:02 ,nw_src=10.0.0.1,nw_dst=10.0.0.2,nw_tos=0,icmp_type=8,icmp_code=0
actions=output:"s1-eth2"
cookie=0x0, duration=2.282s, table=0, n_packets=1, n_bytes=98,
idle_timeout=10, hard_timeout=30, priority=65535,icmp,in port="s1-
eth2",vlan_tci=0x0000,dl_src=00:00:00:00:00:02,dl_dst=00:00:00:00:00:01 ,nw_src=10.0.0.2,nw_dst=10.0.0.1,nw_tos=0,icmp_type=0,icmp_code=0
actions=output:"s1-eth1"
Here we see two flows (one in each direction) in the switch as the result of the ping from h1 to h2. Specifically, dl_src and dl_dst are the MAC addresses (dl=’data link’) and the ‘actions’ tells the switch to output the packet on s1-eth1 for the packet from h2 to h1 or s1-eth2 for the packet from h1 to h2. You can also see the network-layer addresses in the flows (nw=’ network’).
Assignment
Modify the supplied l2fw.py framework to implement a simple layer 2 firewall that will drop packets sent to/from the MAC address pairs specified in the policy file.
First, verify the behaviour of the environment without the firewall module:
Run Mininet:
sudo -E mn --topo single,3 --mac --switch ovsk --controller remote
In another SSH window, run the POX controller with the l2_learning module:
$ cd ~/pox
$ python3 pox.py forwarding.l2_learning
Test connectivity:
mininet> h1 ping h2
PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data.
64 bytes from 10.0.0.2: icmp_req=1 ttl=64 time=45.9 ms
64 bytes from 10.0.0.2: icmp_req=2 ttl=64 time=0.095 ms
^C
--- 10.0.0.2 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1005ms
rtt min/avg/max/mdev = 0.095/23.021/45.947/22.926 ms
mininet> h2 ping h3
PING 10.0.0.3 (10.0.0.3) 56(84) bytes of data.
64 bytes from 10.0.0.3: icmp_req=1 ttl=64 time=44.2 ms
64 bytes from 10.0.0.3: icmp_req=2 ttl=64 time=0.099 ms
^C
--- 10.0.0.3 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 0.099/22.161/44.224/22.063 ms
mininet>
You should be able to ping between all hosts. (You can also test with pingall).
How to get started
1. Create a new folder for the POX module you will create:
$ mkdir ~/pox/pox/comp4911
Put the l2fw.py file from Moodle in ~/pox/pox/comp4911
2. Also put l2fw-policy.csv, the firewall policy file, in ~/pox/pox/comp4911. This file contains a line of text for each rule, with the source and destination MAC addresses separated by a comma e.g.:
00:00:00:00:00:01,00:00:00:00:00:02
00:00:00:00:00:02,00:00:00:00:00:01
These are the (source, destination) pairs for which traffic will be blocked.
3. Examine l2fw.py and read the comments carefully.
4. To run POX with the firewall module added:
$ python3 pox.py forwarding.l2_learning comp4911.l2fw
5. To run POX with debugging output:
$ python3 pox.py –-verbose forwarding.l2_learning comp4911.l2fw
6. Your task is to a) load the firewall rules from l2fw-policy.csv and b) send the rules to the switch. See the skeleton l2fw.py file to get started. You should to add code to
__init__(), _handle_ConnectionUp(), and installRule(). Make your
modifications and then run POX with your l2fw.py module as above. Remember that your l2fw.py must be in pox/pox/comp4911.
7. Use ‘dpctl dump-flows’ to see the rules in the switch. They should be consistent with your firewall rules. For example, this rule drops frames with source address 00:00:00:00:00:01 and destination address 00:00:00:00:00:02.
mininet> dpctl dump-flows
*** s1 ----------------------------------------------------------
cookie=0x0, duration=246.423s, table=0, n_packets=5, n_bytes=322, dl_src=00:00:00:00:00:01,dl_dst=00:00:00:00:00:02 actions=drop
8. You may find it helpful to use log.info() and/or log.debug() to output information about what your module is doing.
9. Test your firewall using ping in Mininet. Hosts that are not restricted by the firewall should be able to communicate, while hosts that are restricted by the firewall should not be able to communicate.
10. Try adding more rules and more hosts to your Mininet topology. Everything should still work.
What to hand in
1. Your l2fw.py file.
2. Your l2fw-policy.csv file.
3. A short design document explaining what you have done and that your firewall both blocks traffic as specified in the policy file and allows other traffic.
4. The output of ‘dpctl dump-flows’ that shows your firewall rules in the switch.
2024-04-12