EEEM048: Internet of Things Semester 1 2022/3
Hello, dear friend, you can consult us at any time if you have any questions, add WeChat: daixieit
Faculty of Engineering & Physical Sciences
School of Computer Science and Electronic Engineering
Department of Electrical and Electronic Engineering
Postgraduate Programmes in Electrical and Electronic Engineering
EEEM048: Internet of Things
FHEQ Level 7 Examination
Semester 1 2022/3
1.
(a) Consider the Wireless Sensor Network shown in Figure 1(a). Describe the role of the component marked as N1 in the figure and explain what IP-based protocol can be suitable to be used for constrained nodes in the network.
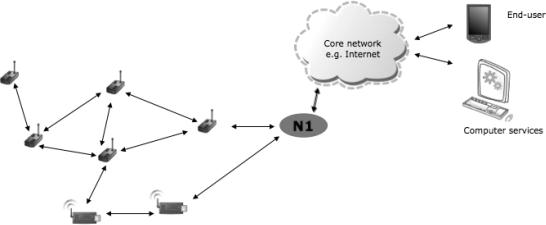
Figure 1(a). A simple Wireless Sensor Network with core network connectivity. [20%]
(b) Consider a MAC algorithm that runs off the radio subsystem on a sensor node with the Contiki Operating System. Assume that the radio subsystem needs to be set off on a periodic basis, but an OS function enables the radio sub-system to complete communication before it enters a sleep state. Write a pseudo algorithm for a process that can provide this functionality. [20%]
(c) Explain the heterogeneity and interoperability issues in dealing with the Internet of Things data and observations and measurements that are collected from the physical world using Sensor Networks. Discuss how Semantic Technologies can help to overcome the heterogeneity and interoperability issues. [20%]
(d) What is the specific format used in the code snippet shown in Figure 1(d) below and where this format can be used?
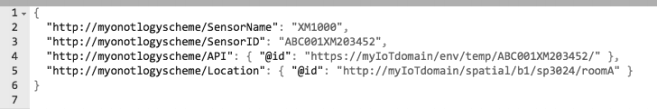
Figure 1(d). Snippet Code [10%]
(e) Consider the following Time Series Data (x): 2, 2, 4, 5, 7, 7, 6, 4, 4, 3. Calculate the standardised z-score of the time series. [10%]
(f) Consider the following ContikiOS process code shown in Figure 1(f).
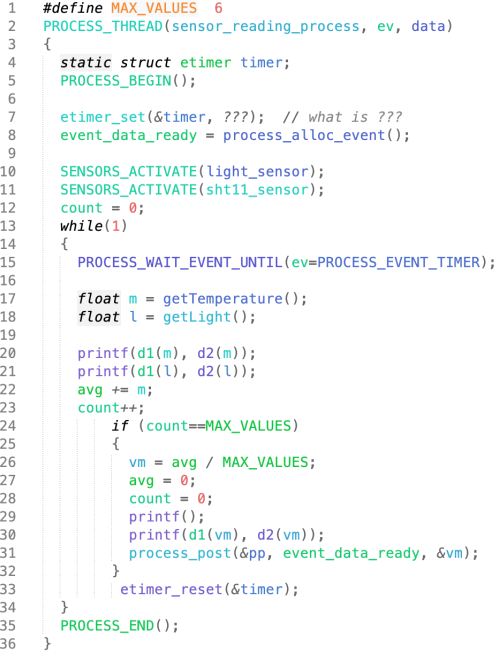
Figure 1(f). A process in ContikiOS
where d1 is the integer function, and d2 is the float function used for printing floating-point numbers. Which instruction should be added instead of ‘???’ in line 7 of the process? What does the process calculate and print? (Your answer can be completed in about 150 words) [20%]
2.
(a) In a smart agriculture application, you have a house at the corner of a 600-meter by 600-meter farm. The home has access to the internet through an optical fibre cable connected to the home gateway. In the middle of the farm, another gateway (i.e., the battery-powered farm gateway) supports four wireless sensors evenly distributed within the farm. Each sensor is required to transmit at a data rate of 300 kbps. The gateways can support two communication protocols, i.e., one for the fronthaul and one for the backhaul, while the sensors can support only one protocol. All the equipment can support IEEE 802.11a, IEEE 802.11ah, IEEE 802.3, and IEEE 802.15.3 communication protocols. What is the best protocol to be considered for each of the following links with justification?
(i) The backhaul between the home gateway and the Internet.
(ii) The link between the home and farm gateways.
(iii) The link between the sensors and the farm gateway. [15 %]
(iv) Considering OFDM modulation with 24 subchannels per symbol, 32 μs symbol duration, 8 μs guard interval, ½ coding rate, and M order modulation, what is the modulation order, M, for each of the following links:
(1) between the sensor and the frame gateway.
(2) between the farm and home gateways. [10 %]
(b) You are required to design a LoRaWAN network for monitoring and controlling purposes in an industrial environment.
(i) In about 200 words, describe the operation principle for Class A, Class B, and class C end nodes and the main differences between them with the aid of illustration figures for potential receive windows. [20%]
(ii) You can use either Class A, Class B, or class C for the end nodes in your network. Select the appropriate class for the following IoT devices and justify your selection:
1) A temperature sensor that is required to periodically send its measurement and is supposed to work for several years without changing its battery.
2) A fire alarm that is needed to be remotely activated with minimal latency. [10 %]
(c) Direct-to-Satellite (DtS) is a promising methodology for the Internet of things.
(i) In about 200 words, discuss some use cases where DtS IoT can be suitable, the challenges that DtS IoT may face, and one possible technology for DtS. [15%]
(ii) Consider the link budget for FH-LoRa where a gateway is deployed over a low earth orbit (LEO) satellite at an altitude of 600 km. According to the link budget parameters in Table 1(c)(ii) answer the following questions:
(1) Compute the link margin. [Show the intermediate steps for the computations] (2) Is it possible to establish communication over this link? [Justify your answer]
Table 1(c)(ii) Parameters for the link budget
|
Parameter |
Value |
|
Transmitter Gain |
2 dB |
|
Operating Frequency |
868 MHz |
|
Transmitter Power |
18 dBm |
|
Polarization Loss |
3 dB |
|
Radius of the Earth |
6371 Km |
|
Receiver Sensitivity |
-137 dBm |
|
Elevation Angle |
40 degrees |
|
Other Losses |
Last digit in your URN (e.g., 3 dB for URN 6862203) |
|
Received Antenna Gain |
3 dB |
3.
(a) In an Industrial IoT application, a temperature sensor is to be used to monitor the temperate of a chemical material in a container. The sensor can produce a minimum voltage of 0V when the temperate in the container is at –20.4oC and produce a maximum voltage of 5V when the temperature in the container is at 184.4oC. The voltage increases linearly as the temperature increases, and the output voltage has an error of ±0.01V.
It is known that the system requires the temperature resolution and accuracy to be at least 0.05oC and of ±0.1oC respectively. As an IoT engineer, you are asked to design an ADC for the sensor to digitize the temperature measure. Explain whether the required resolution and accuracy are achievable, and how. Justify your answer. [20 %]
(b) In the IEEE 802.15.4 standard, the CSMA-CA algorithm is used to avoid collision.
Consider unslotted CSMA-CA with a situation where three devices have transmitted their packet at the same time causing a transmission collision. At the time of the collided transmission, the BE and aMaxBE settings of all devices are 1 and 4 respectively. What is the probability that the next transmission on the channel is a successful transmission? Show your working. [20 %]
(c) An IoT network has been deployed in a farm to monitor the PH level of the soil. The network consists of 8 nodes. The network topology is shown in the following figure where the solid line indicates a radio link between two nodes. AODV is implemented in the network.
Assume that the network has been idle for a long period of time. At a particular time, Node-A has generated a packet addressing to Node-E. Describe the route entries established at Node-C, Node-D, Node-E and Node-F after the delivery of the packet. Show your working.
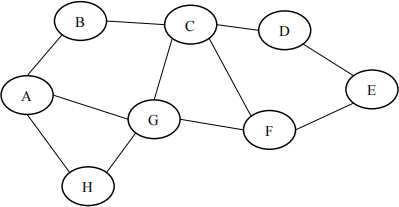
[20 %]
(d) An engineer has developed a sensor node to detect the movement of a bridge. A number of sensors are deployed along the bridge. A gateway is deployed in the middle of the bridge so that all sensor nodes can communicate directly with the gateway. Each sensor node is programed to periodically sense and buffer the movement readings in the background process. Based on a test, the sensor node draws IO mA on average with the background process.
Additional to the background process, for every 10 minutes, the sensor node is also required to transmit the movement readings in the buffer to the gateway. The transmission will last for TD seconds and draw additional ID mA. A battery pack is installed for each node with a capacity of CB in mAh. Derive CB in terms of IO, ID and TD such that the sensor node can operate for at least 356 days. [20 %]
(e) A factory is implementing an IoT solution to control the humidity of a separate warehouse located next to the factory. To integrate the solution into existing infrastructure, the IoT solution provider has proposed to use WiFi technology to build the IoT network since it is possible for the WiFi signal to reach the exiting network in the factory. The data collected from the warehouse can then be streamed to data servers located in the factory for analysis. Based on the proposed design, identify two vulnerabilities of the solution and suggest a protection to overcome each vulnerability. [20 %]
2024-01-09