CS21SN Secure Network Services Sample Paper 2
Hello, dear friend, you can consult us at any time if you have any questions, add WeChat: daixieit
CS21SN Secure Network Services
Answer ALL questions. There are TEN questions each worth 10 marks.
Question 1.
In modern packet-switched networks, including the Internet, the source host segments long, application-layer messages (for example, an image or a music file) into smaller packets and sends the packets into the network. The receiver then reassembles the packets back into the original message. We refer to this process as message segmentation. The following figure illustrates the end-to-end transport of a message with and without message segmentation. Consider a message that is 8 * 106 bits long that is to be sent from source to destination in the following figure. Suppose each link in the figure is 2 Mbps. Only consider the transmission delay here.
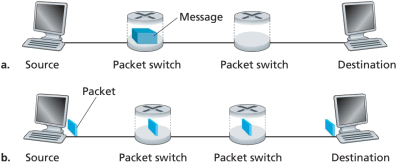
End-to-end message transport: (a) without message segmentation; (b) with message segmentation
a) Consider sending the message from source to destination without message segmentation. What is the total time to move the message from source host to destination host? Show your working. (2 marks)
b) Now suppose that the message is segmented into 800 packets, with each packet being 10K bits long. How long does it take to move the first packet from source host to the first switch? At what time will the second packet be fully received at the first switch? Show your working. (2 marks)
c) How long does it take to move the file from source host to destination host when message segmentation is used? (3 marks)
d) Think about, in addition to reducing delay, other advantages or reasons to use message segmentation, as well as any drawbacks of message segmentation. (3 marks)
Question 2.
IPsec is a suite of protocols for securing networks.
a) Briefly outline how it provides confidentiality and integrity. (2 marks)
b) Briefly explain Authentication Header (AH) and an Encapsulating Security Payload (ESP). (4 marks)
c) “IPSec is not secure”. Discuss whether you agree with this statement or not. (4 marks)
Question 3.
Consider the following network setup. Suppose that the ISP instead assigns the router the address 188.76.19.7 and that the network address of the home network is 192.140.1/24.
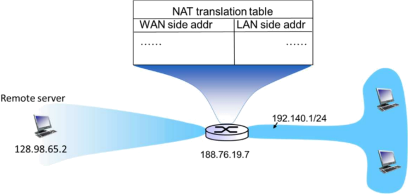
a) Assign addresses to all interfaces in the home network. (2 marks)
b) Suppose each host has two ongoing TCP connections, all to port 21 on host 128.98.65.2. Provide the corresponding entries in the NAT translation table. (4 marks)
c) For one of the TCP connections in question b), describe the IP and TCP headers content (in terms of addresses and port number fields) for the messages routed from the host to the FTP server and back. (4 marks)
Question 4.
The following is a diagram of the TCP/IP stack.
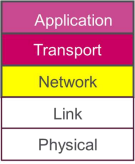
Discuss how to provide security at each layer above the physical layer. (10 marks)
Question 5.
Consider three LANs interconnected by two routers, as the following figure illustrates.
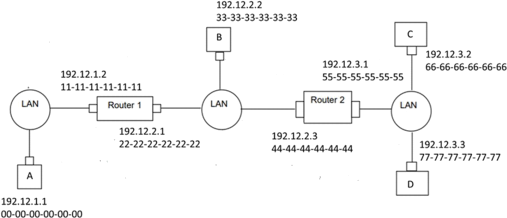
a) Consider sending an IP datagram from Host C to Host A. Suppose all of the ARP tables are up to date. Enumerate all the steps as the message is routed (consider the network and link layer). (3 marks)
b) Consider sending an IP datagram from Host C to Host A now assuming that the ARP table in the sending host is empty (and the other tables are up to date). (3 marks)
c) Now we replace router 1 with a switch S1.
i) Consider sending an IP datagram from Host C to Host D. Will Host C ask router R2 to help forward the datagram? Explain your answer. (2 marks)
ii) Suppose D would like to send an IP datagram to A, and assume that D’s ARP cache does not contain A’s MAC address. Will D perform an ARP query to find A’s MAC address? Explain your answer. (2 marks)
Question 6.
a) Provide a filter table for a stateless firewall that is restrictive as possible but achieves the following:
- Allows all internal users to establish HTTP with any external hosts but block FTP.
- Allow external users to browse the company web page at 45.123.2.123
- Block all other inbound and outbound traffic.
(8 marks)
b) Explain the difference between packet filters and application layer proxies. (1 marks)
c) Can a stateless firewall block TCP connection initiation requests from an external location to any local host, but at the same time allow returning traffic from connections initiated by local hosts? Why or why not? (1 marks)
Question 7.
Describe how to carry out an ARP cache poisoning attack, and how a successful attack can be used to execute further harm within an attack on a computer network. (10 marks)
Question 8.
Discuss the issues and solutions (using a network diagram) related to the interworking of IPv6 and IPv4. (10 marks)
Question 9.
Consider a datagram network using 32-bit host addresses. Suppose a router has four links, numbered 0 through 3, and packets are to be forwarded to the link interfaces as follows:
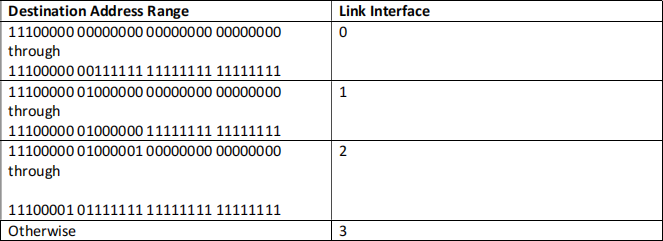
a) Provide a forwarding table that has five entries, uses longest prefix matching, and forwards packets to the correct link interfaces. (4 marks)
b) Describe how your forwarding table determines the appropriate link interface for datagrams with destination addresses:
11001000 10010001 01010001 01010101
11100001 01000000 11000011 00111100
11100001 10000000 00010001 01110111
(6 marks)
Question 10.
Describe how you would carry out a general penetration test on a computer network running networked application services. Use examples to illustrate your points. Discuss how the penetration test can be used to improve security. (10 marks)
2023-12-27