CS21SN – Secure Network Services
Hello, dear friend, you can consult us at any time if you have any questions, add WeChat: daixieit
College of Engineering and Physical Sciences
CS21SN - Secure Network Services
OPEN BOOK Takeaway Assessment
[SAMPLE PAPER]
Please make sure you have read all the documentation provided on Blackboard before starting your assessment.
This assessment is to be completed and uploaded to the appropriate module on Blackboard using TURNITIN, within 24 hours from the time of release.
Date and time of release: 12:00pm (GMT), XXXXXX
Final submission Time: 12.00pm (GMT) XXXXXX
General Instructions to Candidates
1. We recommend you that you download a copy of the Take-Away paper, so you do not need to continue to access the internet.
2. Staff will be available to answer questions ONLY related to the academic content of this assessment between the following times, 12:00pm-3:00pm BST XXXXXX and 9:00am -12:00pm XXXXXX.
3. Please check Blackboard announcements regularly during the assessment duration for any additional information staff may send out.
4. Ensure you have added your candidate number to each page as well as the page number.
5. Any scanned documents/graphs/drawings/hand-written answers must be
incorporated into the answer booklet and it is your responsibility to make sure that this material is legible.
6. Once you have completed your assessment please upload your answer via Turnitin or Blackboard.
Specific Assessment Instructions to Candidates
1. Answer all TEN questions.
2. All questions carry equal marks
Materials provided
1. Answer booklet
Academic Malpractice Statement
As with all graded assessments, you are required to undertake this assessment individually and adhere to the University regulations related to Academic practice. For your information, and awareness, below are two statements describing academic malpractice.
For your information, and awareness, below are statements describing plagiarism and collusion.
PLAGIARISM: “where a student uses, without acknowledgment, the work of other people and presents it as their own which may give an unfair advantage over others. Intentional and unintentional acts of plagiarism (whether reckless or otherwise) will be construed as offences. ”
COLLUSION: "where two or more people have worked together without permission to produce a piece of work which is then submitted for assessment as the work of only one person, which may give an unfair advantage over others. Action maybe taken against a student who has allowed their work to be used as well as against a student who submits work resulting from collusion. "
By submitting my assignment, I declare that:
I have personally prepared this assignment and that it has not previously, in whole or in part, been submitted for THIS, OR any other degree or qualification.
The work described here is my own, carried out personally by me unless otherwise stated.
Where applicable all sources of information, including quotations, are acknowledged by means of reference, both in the final reference section, and at the point where they occur in the text.
I understand that plagiarism and collusion are regarded as offences within the University’s Regulations on Student Discipline and may result informal disciplinary proceedings.
I understand that by submitting this assessment, I declare myself fit to be able to undertake the assessment and accept the outcome of the assessment as valid.
Answer ALL questions. There are TEN questions each worth 10 marks.
Question 1. This question is about Networking Concepts.
a) Why are standards important for protocols? (3 marks)
b) Suppose there is exactly one packet switch between a sending host and a receiving host. The transmission rates between the sending host and the switch and between the switch and the receiving host are R1 and R2, respectively. Assuming that the switch uses store-and-forward packet switching, what is the total end-to-end delay to send a packet of length L? (Ignore queuing, propagation delay, and processing delay.) (2 marks)
c) What are the five layers in the Internet protocol stack? What are the principal responsibilities of each of these layers? (5 marks)
Question 2. This question is about Application Protocols.
Design and describe an application-level protocol to be used between an automatic teller machine and a bank’s centralized computer. Your protocol should allow a user’s card and password to be verified, the account balance (which is maintained at the centralized computer) to be queried, and an account withdrawal to be made (that is, money disbursed to the user). Your protocol entities should be able to handle the all-too-common case in which there is not enough money in the account to cover the withdrawal. Specify your protocol by listing the messages exchanged and the action taken by the automatic teller machine or the bank’s centralized computer on transmission and receipt of messages. Sketch the operation of your protocol for the case of a simple withdrawal with no errors, using a sequence diagram. Explicitly state the assumptions made by your protocol about the underlying end-to- end transport service. (10 marks)
Question 3. This question is about the transport layer.
a) Consider a server that receives a request within a UDP packet and responds to that request within a UDP packet (for example, as done by a DNS server). If a client with IP address X spoofs its address with address Y, where will the server send its response? (2 marks)
b) How is a UDP socket fully identified? What about a TCP socket? What is the difference between the full identification of both sockets? (3 marks)
c) Is it possible for an application to enjoy reliable data transfer even when the application runs over UDP? Explain. (2 marks)
d) Suppose a process in Host C has a UDP socket with port number 6789. Suppose both Host A and Host B each send a UDP segment to Host C with destination port number 6789. Will both of these segments be directed to the same socket at Host C? If so, how will the process at Host C know that these two segments originated from two different hosts? (3 marks)
Question 4. This question is about transport layer security.
Describe THREE attacks that exploit vulnerabilities at the transport layer. Compare and contrast what is required to carry out these attacks, and what malicious outcomes are achieved. (10 marks)
Question 5. This question is about the distributed denial of service.
Suppose that a 12-server web site is subjected to a SYN distributed denial of service (DDOS)
attack carried out by a hacker who uses 6 zombie PCs to send 25-byte SYN packets to the attacked network.
Suppose that each web-site server maintains a table for 1024 TCP connection requests, and that in response to a fake SYN, these servers send a SYN-ACK packet four times, at t = 13s time intervals, then purge the request from the table.
a) What is the minimum per-zombie rate of SYN packets that will cause a denial of service attack? (7 marks)
b) How much bandwidth does each zombie use to perpetrate this attack? (3 marks)
Question 6. This question is about IP Addressing.
Consider the router and the three attached subnets below (A, B, and C). The number of hosts is also shown below. The subnets share the 24 high-order bits of the address space: 147.51.76.0/24.
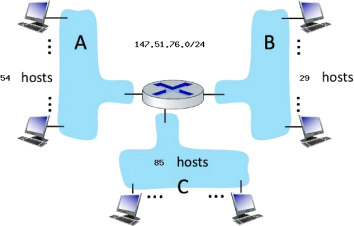
a) Assign subnet addresses to each of the subnets (A, B, and C) so that the amount of address space assigned is minimal, and at the sametime leaving the largest possible contiguous address space available for assignment if a new subnet were to be added. Then answer the questions below. (6 marks)
b) What is the broadcast address of subnet A? (2 marks)
c) What is the ending address of subnet C? (2 marks)
Question 7. This question is about routing algorithms.
a) Compare and contrast distance state vector algorithms with link state routing algorithms (4 marks)
b) Consider the following network graph, and calculating shortest paths for node U:
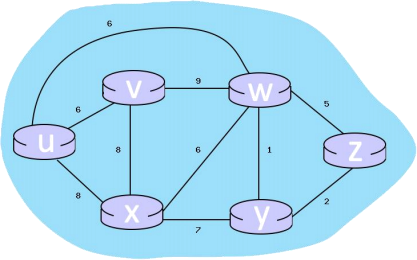
i) What is the shortest distance to nodev and what node is its predecessor? (2 marks)
ii) What is the shortest distance to nodey and what node is its predecessor? (2 marks)
iii) What is the shortest distance to nodew and what node is its predecessor? (2 marks)
Question 8. This question is about network layer security.
Describe the IPSec protocol and discuss its effectiveness in securing computer networks. (10 marks)
Question 9. This question is about network penetration testing.
Compare and contrast the stages of reconnaissance and scanning in a penetration test. Consider their objectives, effort required, effectiveness, detection and ease to prevent. Use examples to illustrate your discussion. (10 marks)
Question 10. This question is about network defence.
Using illustrative examples of how the two controls: firewall and intrusion detection systems operate. Discuss why they are used together in network security solutions. (10 marks)
2023-12-26