CE235 Computer Security 2023-2024 Blockchain and Mining with Proof-of-work for Bitcoin
Hello, dear friend, you can consult us at any time if you have any questions, add WeChat: daixieit
Assignment 2: Blockchain and Mining with Proof-of-work for Bitcoin
CE235 Computer Security
2023-2024
1. Introduction
1.1 Bitcoin Mining
Bitcoin is a cryptocurrency. In the Bitcoin system Bitcoins are mined through proof-of-work mechanism. Bitcoin miners are given technical puzzles to solve. There is only one puzzle at any time with a given difficulty level, which is set by the system administrator. New puzzles are created after the current one is solved.
The first miner who solves the puzzle is awarded a specified number of bitcoins. The winner creates and sign a new block with digital signature technology and broadcast to other Bitcoin users. The signed block is linked to the previous signed blocks. These blocks form a chain of blocks (called blockchain) as shown in the following figure. The new signed blocks are verified by others and could become mature after being confirmed by a given number of miners, which is measured by length of blocks linked to the new blocks.
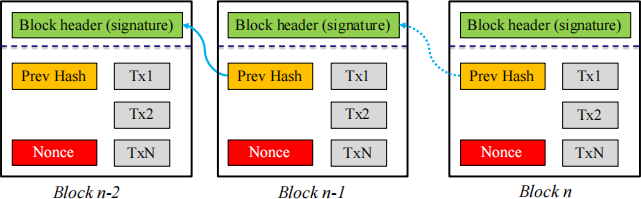
1.2 Technical puzzle
The puzzle set in the proof-of-work is to find a specific integer number (called nonce), which together with a few other numbers (such as hash value of the previous block, the transactions to be included to the new block)
are hashed with SHA-256 algorithm and the hashed value satisfies a given condition.
The puzzle can be formulated as follows:
|
find nonce, subject to: hash(preHash, nonce, Tx) < levelHard |
where preHashis the hash value of the previous block, Tx is transaction of bitcoins. levelHard is a given number, usually controlled by requiring a consecutive number of most significant bits (MSB) being zeros, for example the first 30 MSBs being zero. The more MSB zeros required on levelHard, the more difficult to solve the puzzle (finding the nonce satisfying the condition). Below gives a binary number with the 15 MSB being zeros and 5 least significant bits (LSB).
(MSB) 00000000000000011100000101111110011010101100000 (LSB)
1.3 Signing and verifying a new block
The first miner solving the puzzle will create a new block, which includes a block header (storing the digital signature of this new block, which will include the hash value of the block body) and a block body. The block body includes the hash value of the previous block, the found nonce and transactions included in this block. The digital signature is created by encrypting the hash value of this new block with private key. The block is linked to the last block of the existing blockchain and broadcast. The new block will then be verified by others using the winning miner’s public key and checking the hash values of this and previous blocks.
2. Specification
This assignment takes 16% of the marks (16 marks) of this module. The aim of the assignment is to write a Python 3 program, which will implement a simplified version of Bitcoin mining and digital signature schemes. Specifically, it includes the following THREE tasks, which is illustrated in the following figure.
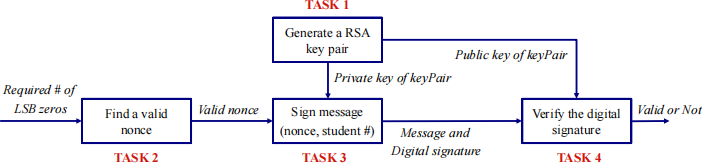
2.1 Task1: Create a RSA public/private key pair with 1024 bits key length [2 marks]
o Hint: you can simply use the provided example (Example 1) in Sample program to generate a RSA key pair.
o The RSA key pairs will be used in Task3 and Task4 of this assignment.
o The created RSA public {n,e} and private keys {n,d} need to be displayed with the following format:
|
Public key: (n=0x995361030caa5bf308e272fe07f3466c0727b5ac0c41107142fd97dd75ec4a197250c038 8b8711b210b2beb300980321913e9eb21b22f72c3fe8b62adda13491c6efbf3f4e6c6c60738da c790af2ca0b8067f4550fae82c8ea85d3fc0667f1de7a193f23a1d30e8e7f2894f07ce26b5d94 85df5a29fc265fc217dbbb91065b35, e=0x10001) Private key: (n=0x995361030caa5bf308e272fe07f3466c0727b5ac0c41107142fd97dd75ec4a197250c038 8b8711b210b2beb300980321913e9eb21b22f72c3fe8b62adda13491c6efbf3f4e6c6c60738da c790af2ca0b8067f4550fae82c8ea85d3fc0667f1de7a193f23a1d30e8e7f2894f07ce26b5d94 85df5a29fc265fc217dbbb91065b35, d=0x24cf1913a7d74042dce7ac6ea30efae19568299bb7c769009ff20ca2ec9c010011eb23f28 f40aa7562bfdebb4f91aef2c091557cf1b9d7b82651a2663115f1ee0c416b1fec516a83657558 068f1eebffae9f11b2801830acf2b0af4367fcd26ffe4672c5c5165afaeb5eeb81e6497a04192 133476e124b4ce2a869a16fc998e1) |
2.2 Task2: Find a nonce which produces a hash value with hash algorithm SHA-256 satisfying requirement of the 8 least significant bits (LSB) being zero. [6 marks]
o Hint: you can extend Example 4 in the provided sample program to complete this task. Example 4 generates only one nonce and check if the nonce is valid.
o You should try many random integers as nonce (with a loop) until you successfully find a nonce that meets the requirement. The only output from this task is the nonce, which needs to be displayed with the following format (suppose the found nonce is 12345):
|
Valid Nonce: 12345 |
2.3 Task3: Digitally sign the nonce and your student number with the RSA private key [4 marks]
o The message to be signed is a string consisting of the nonce and your student number, which are separated by a space. For example, if the found nonce is 12345 and your student number is 54321, then the message to be signed needs to be a string “12345 54321”
o Hint: you should generate the message to be signed (a string with the nonce and your student number), then use Example 2 in the provided sample program to sign the message with RSA key pair generated in Task 1.
o The outputs of this Task3 include the hashed value of the message and the signature, which need to be displayed with the following format.
|
Message: 12345 54321 Hash value of message: 32547436749427615422843012801191259465058592439985110545719463144077305232244 Signature: 0x3ee3934a23e2d55c7377a125e052e5f305d82fbf0643713acb00cf1cb0c968eb65f56de35d0 37aac5d0d3ae7489d4067e9c38ceee2f4f602ebf90d8a070606c27808f22bd537a42e066c86c3 6d5e5efa786be09e0753f82a847a05d0bdcd0418624a3f3c8a203524f97f56528ffca1e633d29 bd8cfa80fb80bc3b4a53e2d51b5 |
2.4 Task4: Verify the message authentication. [4 marks]
o The message authentication is to be verified by decrypting the digital signature with public key {n,e} generated in Task 1 and comparing the hash value obtained from the decryption of the digital signature to that of the signed message.
o The process of verifying the message authentication needs to output yes or no depending on the verification outcome.
o Hint: you can utilize the Example 3 in the provided sample program to complete this task.
3. Sample Program
We provide a sample python program miningBitcoin_sample.py, which includes most of the needed RSA encryption and digital signature functions to complete the above tasks. It can be run from integrated development environments (IDLE). It can also be run from the command line like this:
python mingingBitcoin_sample.py
You should modify the sample python program and add codes to complete the tasks, especially for Task2 on the proof-of-work part. A Google Colab notebook for the sample program is sharedhere.
Your own program should be called something like cs_bitcoin_registrationnumber.py (see naming instructions later). Your program must run from the command line like this:
python cs_bitcoin_registrationnumber.py
The outputs of your program are required to be displayed, following the specified format for marking purposes.
4. How to submit
Submit one python .py file to Faser called:
cs_bitcoin_registrationnumber.py
For example, if your registration number is 1234567, your filename will be:
cs_bitcoin_1234567.py
Note that the filename is a .py file. The file name is all lower case.
5. Marking Scheme
You will be asked by the Dr He or teaching assistants at NWU to demonstrate your work and answer questions to ensure it is your own work. Your marks for this assignment will be dependent on the complement and output results of your program, and your answers to the questions asked by the teachers. If you are asked to but you don’t demonstrate your work, no mark will be given to your assignment work.
Apart from demonstration of your work to the teaching staff members, it is mandatory for you to submit your program file to Faser on time. Otherwise, you may not get any mark for your work on the assignment.
Your submitted program may be checked and tested by Dr He. If there are problems found from the testing, your marks received from your demonstration may be deducted.
Plagiarism
You should work individually on this project. Anything you submit is assumed to be entirely your own work. The usual Essex policy on plagiarism applies:http://www.essex.ac.uk/plagiarism/.
2023-12-01