ACCTG 222 Accounting Information Systems SEMESTER ONE, 2022
Hello, dear friend, you can consult us at any time if you have any questions, add WeChat: daixieit
ACCTG 222 Accounting Information Systems
SEMESTER ONE, 2022
LS Ltd is a small retail shop that sells children’s toys . The owners recently hired a graduate and asked him to prepare a flowchart depicting the company's sales and collection process . Here is his first attempt:
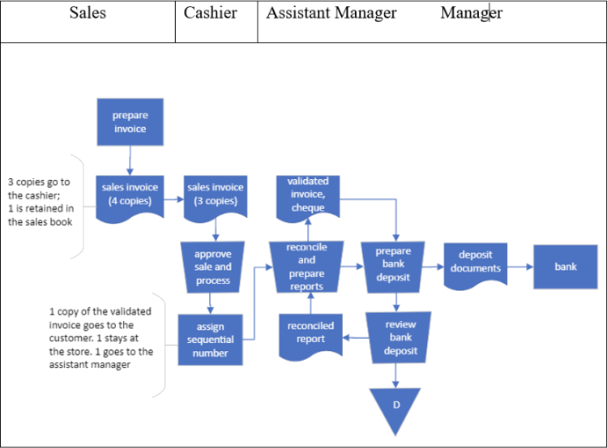
1 Identify at least five weaknesses in the design of the graduate's system flowchart for LS Ltd that do not follow the conventions .
2 Write a memo on how LS Ltd can improve its revenue and cash collection process . Identify the steps involved and who should be performing the task. Include at least five internal controls and explain how each of these controls help reduce risks .
For simplicity, assume that:
· The company cannot hire more people.
· It does not give credit to customers .
· The customers pay for the items and take them home immediately (no shipment).
All purchase requests by the University Library goes through its requisitions department. Staff and students can suggest titles of books , periodicals , and other items via e-mail to the requisition librarian. The requisitions librarian tracks these requests in a database. Once at least ten requests for the same item have come in, the requisitions librarian orders it from a vendor using a standard purchase order. The requisitions librarian e-mails the people who requested for that item to inform them of the order and files a copy of the purchase order by title.
When the item is received, the receiving clerk matches it against the purchase order. If it matches , the item moves out of the receiving department into the library, where it is filed. A copy of the receiving report goes to the requisition librarian and the financial services department.
The financial services clerks match the invoice against the receiving report and purchase order. They also reconcile any differences between them with the vendor. Invoices are paid monthly on the 20th. The financial services clerk creates a payment packet of all relevant documents , stamps “ Paid” on the top, and files it alphabetically by vendor name and date within the vendor file.
3 Create a Data Flow Diagram at the Context Level for this process .
4 Identify two internal control risks in the library’s purchase and expenditure process . Explain why these are risks in this context and suggest one internal control for each of the two identified risks .
Computer Crime is increasing worldwide and is being committed in different forms . Here are a couple of recent events . Use Carter's taxonomy to analyse these events . State the element(s ) of the taxonomy that applies to each event with an explanation for your selection. Discuss how companies can protect themselves from such events in the future.
5 A teenager committed a denial-of-service attack on a telecommunication network’s system .
6 An employee used their previous access into the company's system to lock out other users by changing their passwords .
7 Criminals broke into a retail shop and stole all the store's computers and then hacked into their customer database.
8 A common form of payroll fraud is payments to non-existent employees or to employees that were previously terminated and should no longer be on payroll. Explain how this type of fraud is committed and describe control techniques that can be used to detect or prevent this risk.
9 Identify and clearly describe other key internal controls that should be included to reduce other potential risks in payroll processing.
2023-10-31