Cyber Security Management
Hello, dear friend, you can consult us at any time if you have any questions, add WeChat: daixieitCyber Security Management
Assignment
Autumn 2023
Words:1600
Weighting:40%
Learning Outcomes assessed:1,2,3
Submission date:27 October 2023 (11:59pm UK time)
Module Leader:Chitra Balakrishna
Instructions to candidates:
Assignment Guidance
Submission Requirements
Scenario
The network in a school that caters to students from year 1 to year 13 is fairly basic in terms of infrastructure and services. It was installed in 2015 and hasn’t been upgraded since, except for the replacement of the broadband router with a similar one that has a VPN server. There school building has four floors, with the primary years located on the ground floor.
The building has wired connectivity across classrooms and staff offices. A wired backbone runs through the corridors on each floor, providing interconnectivity to the teachers' desktops in every classroom. This is primarily used for projection and accessing teaching materials stored on a centralised server. Each floor has a switch, and each switch connects to a core switch in the mini data centre located on the ground floor at the back of the building.
The network is connected to a broadband provider for Internet access. Access to the Internet is limited to the desktops in the classrooms and to the staff offices. The mini data centre houses computing, storage servers, and other network equipment, including the broadband router that provides access to the Internet. A VPN server and the school’s web server are also in the data centre.
Students are provided laptops that utilise the WiFi access points within classrooms to access the VLE (virtual learning environment). Students can also access the school-hosted VLE platform remotely from home. This remote VLE access is via a VPN. The VPN server is part of the VPN router and can only support five simultaneous user connections at any given time.
The system administration is handled by a few staff members who are not trained administrators but have learned on the job. No consideration has been given to security, and as a result, there are no specific security practices in place. The only basic access controls are for the VLE resources and network Internet access.
The school has now received an undisclosed amount of funding from an agency concerned with securing the school's online services and assets (including personal student data, school-related data, etc.), as well as ensuring online safety for students.
The security upgrades are expected to be done beginning with conformance to the NCSC’s Cyber Essentials and tested with Cyber Essentials Plus.
The school has approached you – a cybersecurity consultant – to take the school onward to gain a better security posture and improve it.
Assignment
General
Task 1
Given the scenario of the school, you are first required to demonstrate to the school authorities, the potential network security threats that they face:
a) Identify three important services of the school that need to be “available” all the time with a brief description of the service indicating its location in the infrastructure, its access, and use.(10 marks)
b) What are the potential threats to the “availability” of the services and data, in your opinion? What would be the impact if the threat led to an exploit resulting in an incident. Mention the potential causes for it.(5 marks)
c) Include a risk matrix and indicate the risk rating for the risks and mention the levels assigned to each of the risks by including them in a matrix. Mention in brief what is necessary to mitigate the risk posed by the threats.(5 marks)
Task 2
List out the potential issues that require attention from a security perspective. These would be things you would want to check in the school’s existing infrastructure and services, as they are. Categorise them under the headings of network infrastructure, servers and services, and end devices (desktops, laptops, tablets). Use the table format below. It includes two example checks to get you started:
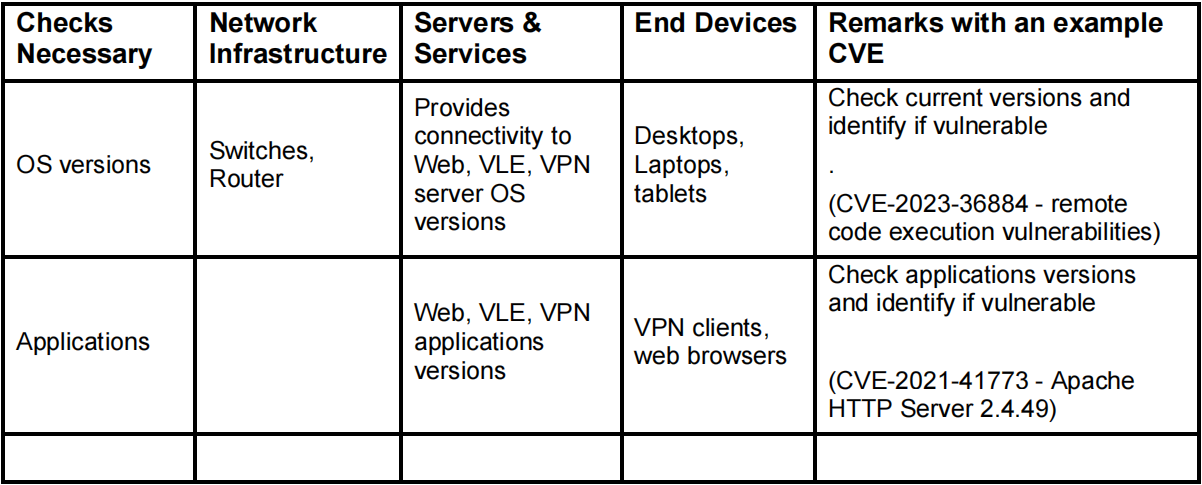
Guidelines for the task: For task above identify aspects of infrastructure – both network and computing (servers and end point devices), and application services that would require examining for secure configuration and function. Also consider how data requires to be kept confidential and check for appropriate functions and implementations necessary to keep data confidential and private.
You can find information about the CVE either on the NVD website or at https://www.cvedetails.com. The CVE you reference could be any recent vulnerability (2020-2023) - for example, the CVE in the top row refers to a remote code execution vulnerability in Windows 11. Feel free to mention a CVE related to vulnerabilities in any operating system of your choice.
Task 3
b) List the controls you would recommend implemented in the context of the school’s infrastructure and services for each theme.(10 marks)
ANSWER EITHER TASK 4 OR TASK 5
Task 4
a) What is the service subscription option that could be suggested for the school given that there are no trained administrators handling their infrastructure?(8 marks)
b) Justify your choice both from the services perspective as well as the security perspective – how would the services used by the school be hosted on the cloud and what aspects of security would be the provider’s responsibility?(12 marks)
Task 5
The school has requested the addition of physical security monitoring and access control for its infrastructure. Cameras would be installed around the periphery and at the entrances/exits to monitor the building.
Furthermore, all entrances will have automated door locks requiring a combination of ID card tap plus an individual secret code known by students and staff. Visitors to the school are restricted to the Reception area and Principal's office.
a) Provide a brief description of two typical uses of the physical security system by the school.(6 marks)
b) With this, you have so far listed the Physical and technical controls. What administrative controls might you propose for the context of the school? Note that administrative security controls include any security measures focused on managing people.(14 marks) Total 20 marks
Total marks for the assignment = 100 marks.
Your report should be 1600 words (+/- 10%) plus diagrams.
References do not count towards this word limit. For your prices you need to show via references where the prices have come from so that these figures can be validated. If you use any work which is not yours (for example a picture or a piece of text which helps you to explain your argument) then this must be correctly and fully referenced using the Harvard referencing system.Cyber Security Management
Statement and Confirmation of Own Work
Programme/Qualification name:
All NCC Education assessed assignments submitted by students must have this statement as the cover page or it will not be accepted for marking. Please ensure that this statement is either firmly attached to the cover of the assignment or electronically inserted into the front of the assignment.
2023-09-30