Packet Tracer – AssignmentSS-M8-2023
Hello, dear friend, you can consult us at any time if you have any questions, add WeChat: daixieit
Packet Tracer – AssignmentSS-M8-2023
Topology
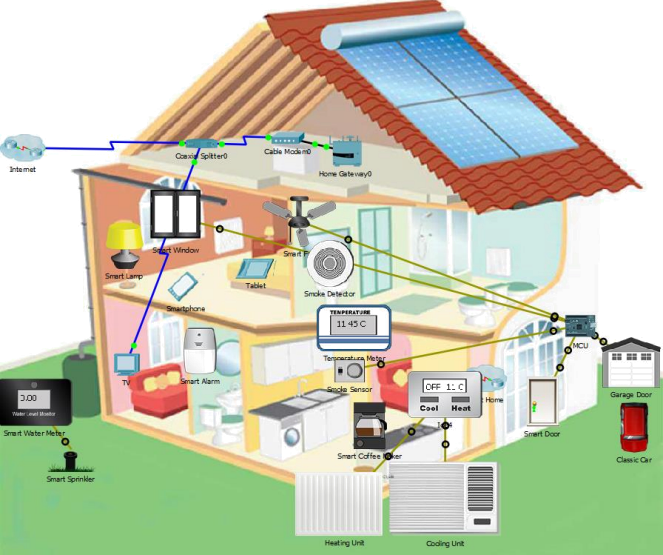
The topology is a home IoT system that has been prototyped in Packet Tracer. It shows a cutaway view of a home with different sensors, actuators, and connections shown.
Objectives
In this Packet Tracer, you will begin the threat modeling process for the device layer of the IoT attack surface.
Part 1: Identifying the Security Objectives
Part 2: Exploring and Diagraming the Physical Network
Part 3: Creating an Inventory of Assets of the Physical Device Attack Surface
Part 4: Identifying Potential Threats with the STRIDE Model
Background / Scenario
A home owner has been reading about the IoT and is very enthusiastic about the capabilities of home automation IoT systems. The home owner wants to install such a system in his house but does not know how to do so. He has contacted a company that can design and install the system. The company focuses on security throughout the system design, provisioning, and development process. They are currently developing a threat model for the system. You have been hired by the company and your first task is to complete the threat model.
The house is 3500 sq . ft. and includes two stories and an attic. The customers are away from home regularly and have requested the safest house possible. The customer wants to be able to remotely monitor the house and wants the following IoT-supported systems:
• Climate control
• Smoke / fire
• Temperature issues out of the normal range
• Door and window locks
• Lawn watering
• Local alarm and emergency department messaging
The system should be controllable locally and through the cloud. The user should be able to access the controller from a web browser from inside the network as well as remotely through a smartphone app. This will allow the customers to monitor or control the system when they are away.
The system should collect and store data from the remote sensors and various actions should take place based on the input from those sensors . For example, if the temperature goes above the maximum range, it probably means the AC is not working and someone needs to be notified ASAP. If the system detects smoke, the local alarm should sound, and the customer and the fire department should be alerted. Data from the system should be retained and analyzed. In addition, the customer should be able to change the threshold values that trigger different actuators and events as necessary, either locally or through the mobile app. The triggers and behaviors, data analytics, and remote-control access are all available through a home automation cloud application service that the system will interface with.
The home owners should have password protected accounts for access to the system. In addition, the company should have access to system diagnostics in case problems occur with the system. Only the homeowner should have access to the cloud applications.
It is also important to make note of these other details of the house:
• 3 bedrooms, 1 den, 2 baths
• 2 stories and an attic
• 1 main front door and 1 side door entry
• 2 sliding doors to the backyard – one coming from the master bedroom
• 2-car garage
The team has designed the system and it is your job to perform threat modeling on the design.
You will start by creating a threat model for system. The home automation system has been prototyped in Packet Tracer. The system is very similar to the home IoT system that you explored earlier in the course . Because the threat modeling process is very detailed, we will be breaking it up into four linked labs. The first three labs are for each layer of the IoT attack surface. In the final Packet Tracer, you will rate the risks and determine how the risks will be managed.
Required Resources
• Packet Tracer 7.1 or later
Part 1: Identifying the Security Objectives
The first activity in the threat modeling process is to establish the security objectives for the system.
Step 1: Provide objectives for each of the six categories.
There are six categories of security objectives that are often used to define the security needs of a system or organization. Answer the questions to help develop these objectives. Answer the questions from the point of view of both the company and the customer, where appropriate.
Identity
Visualize the application and identify the security objectives of this system based on the requirements. What access and authorization controls should be in place to document who is accessing the IoT system?
Should there be any machine-to-machine (M2M) access controls in place?
Financial
Document the financial losses that could occur due to a failure of the system, system components, or security breech.
What is the potential financial impact to the customer if components of the system malfunction?
If a threat actor was able to gain access to the home network in a security breech, what losses could occur?
Reputation
Document any possible impact on the customer’s reputation if the IoT safety/security system is attacked.
What would be the repercussions for the owner if their home-based safety/security system was attacked?
Privacy and Regulation
Document the impact of any privacy concerns as well as regulation requirements for this system. Are there any privacy concerns for any of the data collected or used by this system?
Does the owner care that logs are being kept about their access and movement throughout the house (motion sensors)?
Identify any data that could cause privacy concerns for the owner of this system.
Availability Guarantees
Document the expected availability and guaranteed uptime of the IoT system. Is this system required to be available at all times?
Is there any acceptable downtime that can be tolerated for this system? Explain.
Safety
Document the potential impacts to physical welfare of people and physical damage to equipment and facilities. This is particularly important in industrial control system (ICS) environments.
Part 2: Exploring and Diagraming the Physical Network
Step 1: Open the Packet Tracer Network.
The Packet Tracer network is an interactive demonstration of a home automation IoT network. It is the same network that was used in Chapter 1.
a. Open the Packet Tracer - Threat Modeling at the IoT Device Layer.pka file.
b. Refamiliarize yourself with the devices and topology before proceeding.
Step 2: Diagram the network.
Use the blank floor plans that are included in Appendix A of the PDF version of these Packet Tracer instructions. Diagram the IoT devices on the floor plan. Place the sensors, actuators, and devices at the locations on the floor plan that seem to match the PT network. Label each device .
Part 3: Creating an Inventory of Assets of the Physical Device Attack
Surface
You will now complete an inventory of the devices in the IoT network by entering them into a table.
Step 1: List all the assets.
Fill in the table that is provided in Appendix B of this Packet Tracer with all the IoT device physical assets that are part of the home automation network. Also add the device role.
What are some roles that devices can take in an IoT network?
Step 2: Determine the interactions between assets.
Continue to work in the table from Step 1. Fill-in the relationships between the devices in the Works With column. Which sensors and actuators work together?
|
Device |
Device Role |
Works With |
|
Part 1: Physical Device |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Part 4: Identifying Potential Threats with the STRIDE Model
In this part, you will identify threats using the STRIDE methodology. Try to describe as many threats as possible based on your experience in the course, theOWASP IoT vulnerabilities page, and other information sources.
Use the STRIDE model to create a list of potential threats
Complete this table with threats for each category in the STRIDE threat model. Add potential threats that could occur for each STRIDE category. Include the type of threat using the OWASP terminology where possible.
|
Threat type |
Asset type |
Threats |
|
(S)poofing – can an attacker pretend to be someone he is not, or falsify data? |
Sensors |
|
|
Actuators |
|
|
|
(T)ampering – can an attacker successfully inject falsified data into the system? |
Sensors |
|
|
Actuators |
|
|
|
(R)epudiation – can a user pretend that a transaction did not happen? |
Sensors |
|
|
Actuators |
|
|
|
(I)nformation Disclosure – can the device leak confidential data to unauthorized parties? |
Sensors |
|
|
Actuators |
|
|
|
(D)enial of Service – can the device be shut down or made unavailable maliciously? |
Sensors |
|
|
Actuators |
|
|
Threat type |
Asset type |
Threats |
|
(E)scalation of Privilege – can users get access to privileged resources meant only for admins or superusers? |
Sensors |
|
|
Actuators |
|
2023-06-17